This blog describes my attempts to load public certificates into an Azure Integration account. I am migrating a BizTalk AS2-EDIFACT exchange into Azure. As part of this I need to add a lot of public certificates into an Azure Integration account. This can be done using the azure portal but I wanted do this by script because there is a lot certificates to upload.
The portal experience
Before I move onto my attempts to script loading of certificates, let’s first review the experience using the Azure portal. Opening the certificates blade on the Integration Account, select add, choosing a public certificate type and browsing to the certificate I see.
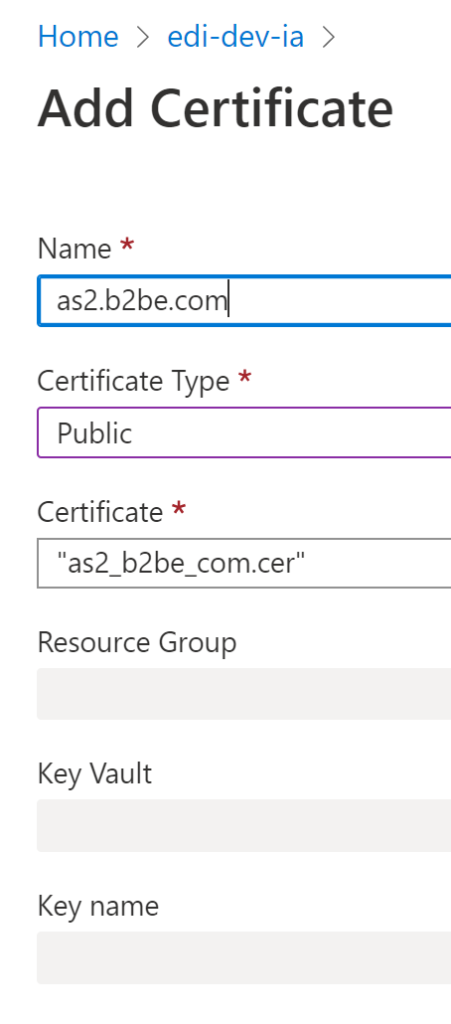
It is important to note that when adding a public certificate the resource group, key vault and key name are greyed out. Furthermore you must use a *cer certificate file to add the certificate. I found that if I tried to use a *.p7b the upload does not work. In the case of a private certificate you must supply the resource group, key vault and key name as well.
Running the powershell cmdlet Get-AzIntegrationAccountCertificate I get
Get-AzIntegrationAccountCertificate -ResourceGroupName "edi-dev-rg" -Name "edi-dev-ia"I see
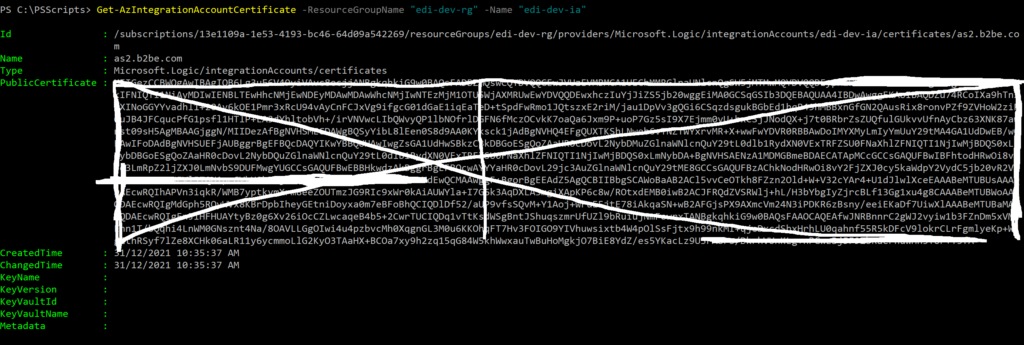
It is noteworthy that KeyName, KeyVersion, KeyVaultId and KeyVaultName are empty.
Powershell scripting
I choose PowerShell over the arm template approach because I foresaw that changing a certificate would be easier. Powershell will read the certificate file from a folder. Thus changing the certificate is simply a matter of the replacing the certificate file in a folder.
I started with the following Powershell code which follows the Microsoft documentation.
$RG = "edi-dev-rg"
$IA = "edi-dev-ia"
$keyvaultid = "/subscriptions/blah-blah-blah/resourceGroups/edi-dev-rg/providers/Microsoft.KeyVault/vaults/edi-dev-kv"
$IACertName = "as2.b2be.com"
$KeyName = "as2b2becom"
New-AzIntegrationAccountCertificate -ResourceGroupName $RG -Name $IA -CertificateName $IACertName -KeyName $KeyName -KeyVersion "1.0" -KeyVaultId $keyvaultid -PublicCertificateFilePath "C:\Customer Certificates\B2BE\as2_b2be_com.cer"This gave the following error.
New-AzIntegrationAccountCertificate: C:\PSScripts\AddNewCert2IA.ps1:6
Line |
6 | New-AzIntegrationAccountCertificate -ResourceGroupName $RG -Name $IA …
| ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
| {"error":{"code":"BadParameter","message":"Method GET does not allow operation '1.0'"}}On changing the script to
New-AzIntegrationAccountCertificate -ResourceGroupName $RG -Name $IA -CertificateName $IACertName -KeyName $KeyName -KeyVersion " " -KeyVaultId $keyvaultid -PublicCertificateFilePath "C:\Customer Certificates\B2BE\as2_b2be_com.cer"
the error goes away and I get a different error.
New-AzIntegrationAccountCertificate: C:\PSScripts\AddNewCert2IA.ps1:7
Line |
7 | New-AzIntegrationAccountCertificate -ResourceGroupName $RG -Name $IA …
| ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
| {"error":{"code":"KeyNotFound","message":"A key with (name/id) as2b2becom was not found in this key vault. If you recently deleted this key you may be able to
| recover it using the correct recovery command. For help resolving this issue, please see https://go.microsoft.com/fwlink/?linkid=2125182"}}How do I fix this error? If you load a public certificate to an integration account then you must leave the KeyVersion, KeyVaultId and KeyName out of the script. This works.
New-AzIntegrationAccountCertificate -ResourceGroupName $RG -Name $IA -CertificateName $IACertName -PublicCertificateFilePath "C:\Customer Certificates\B2BE\as2_b2be_com.cer"
Finally the script I use to upload all of my public certificates from a common folder is
#AddNewCert2IA.ps1
Get-ChildItem "$(System.DefaultWorkingDirectory)/$(edi.templatesPath)/edi-supplier-biztalk-certs-ia/" -Filter *.cer |
Foreach-Object {
$IACertName=[io.path]::GetFileNameWithoutExtension($_)
$IACertFileName=$_
Write-Host "Re-Deploying cert:$IACertName from file:$IACertFileName"
try
{
#throws an error if the certifcate does not exist
Set-AzureRmIntegrationAccountCertificate -ResourceGroupName "edi-$(edi.env)-rg" -Name "edi-$(edi.env)-ia" -CertificateName $IACertName -PublicCertificateFilePath "$(System.DefaultWorkingDirectory)/$(edi.templatesPath)/edi-supplier-biztalk-certs-ia/$IACertFileName" -ErrorAction Stop -Force
}
catch
{
Write-Host "Deploying cert:$IACertName from file:$IACertFileName"
New-AzureRmIntegrationAccountCertificate -ResourceGroupName "edi-$(edi.env)-rg" -Name "edi-$(edi.env)-ia" -CertificateName $IACertName -PublicCertificateFilePath "$(System.DefaultWorkingDirectory)/$(edi.templatesPath)/edi-supplier-biztalk-certs-ia/$IACertFileName"
}
}

