I show an issue I faced in moving all our customers to use SFTP on Blob. A long time ago I gave a talk on this on Integration DownUnder. I have been meaning to write a blog about this, but I want to talk about a problem here.
SFTP on Blob
I have been busy migrating all our customer from using a on-premises FTP server to a SSH File Transfer Protocol (SFTP) support on Azure Blob Storage.
The before picture is

The after picture is

To set up firewall inclusions on the Blob Store the first step was to set managed system identity on all our Logic Apps and Azure functions. The second step is to specify resource instances that will have access to your storage account based on their system-assigned managed identity.
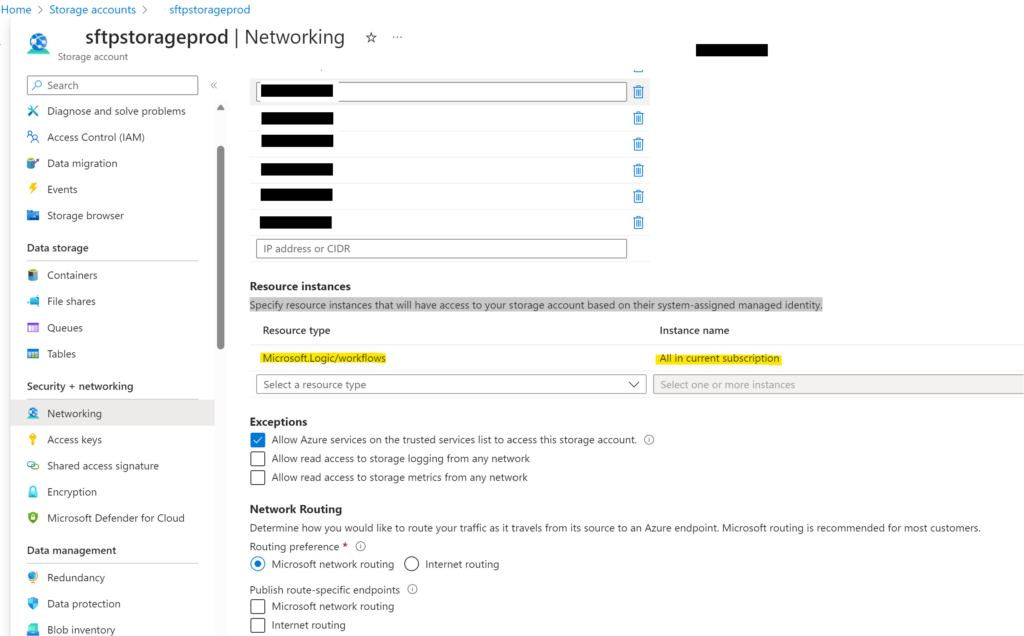
The third step was to include all the customer IP addresses. This has been working well.
The problem
A customer rang up saying that while he could connect to our SFTP from his local laptop, he was unable to connect from his server hosted in Azure. Sure, enough when I check the Log Analytics for the SFTP on Blob I saw.
It is noteworthy that all the IP addresses are private IP addresses and is not public ones. This was the private IP address of the VM hosted in Azure.
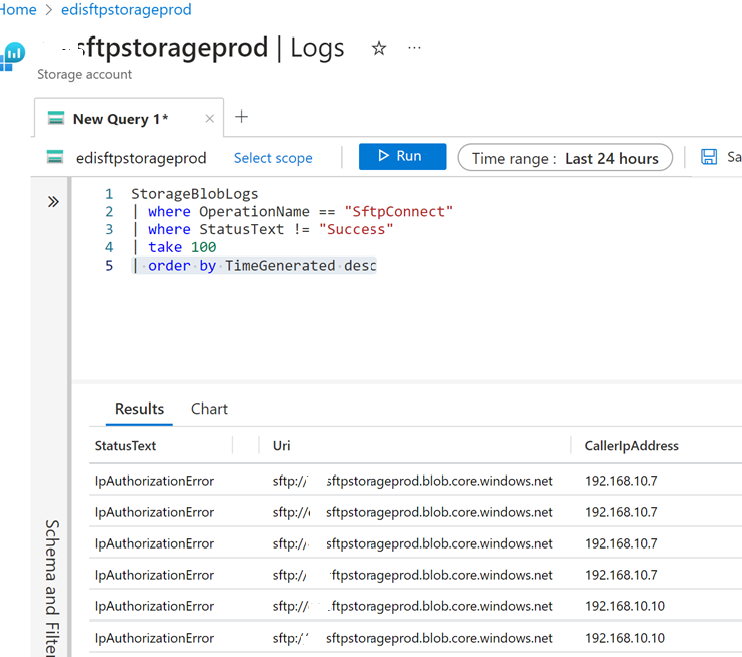
Thus, Azure is clever enough to realise that it is part of the same large Microsoft Azure region and tries to connect without going out to the internet.
The solution
Change the routing preference of the VM and then it goes via the internet. The VM routing preference was Microsoft Network
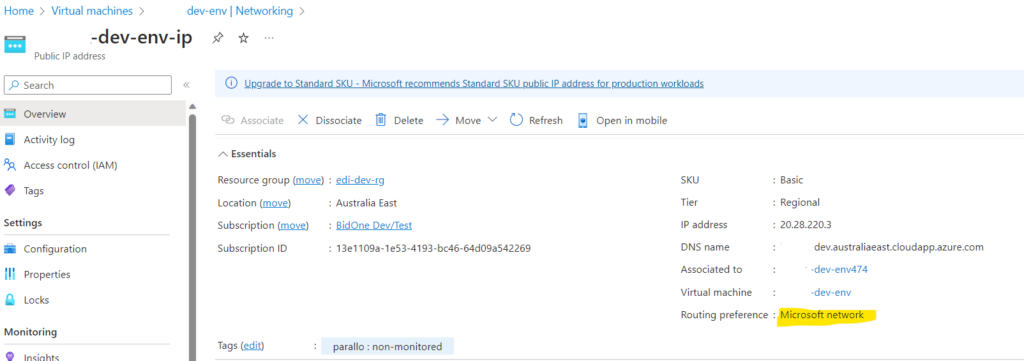
Changing this to Internet solves this issue. See Tutorial: Configure both routing preference options for a virtual machine – Azure portal | Microsoft Learn
Postscript
Tony created product feedbacks in this blog here, if you do not mind, could you please upvote them?
https://feedback.azure.com/d365community/idea/3377b609-b852-ee11-a81c-002248544521
https://feedback.azure.com/d365community/idea/ed929835-b652-ee11-a81c-002248544521

